Diesen Artikel auf Deutsch lesen.
It's been a long time since the Rolling Stones were telling people "Get Off of My Cloud", and times have certainly changed; nowadays, we move more and more "into the Cloud". But what seems so simple for people privately can cause quite the headache in a professional context. Especially when it comes to sensitive topics such as data protection or information security in general. And so it's not surprising that in many countries, many companies that are considering moving their operations into the Cloud are hesitant at first. Questions about topics like security and performance weigh heavily on the minds of the decision-makers.
These concerns are understandable, as there have been repeated discussions and negative examples in the past. Reason enough for Seibert Media to take a closer look - and to do some "myth-busting"! Because many things you might think you know about the Cloud are not accurate (anymore). And one thing is clear: the future is looking up!
So join us in a journey into the clouds and read in our first article in our "Cloud Mythbusters" series what security and compliance are like in the Atlassian Cloud (which, by the way, is not limited to the Atlassian Cloud!). The other articles will deal with the following topics:
- Put on a performance!
- Bye-Bye Server Apps – Hello Cloud?
- Should I Change Anything in My Change Management?
- What Happens to my Data?
- What Does My Admin do When There's Less Admin to Admin?
- Can I still Customize my Cloud Instance?
- Will Cloud Still Work Well When My Company Gets Bigger?
In every blog article, we'll get to the bottom of each myth together, and we'll see what's left of them afterwards… And now: enjoy reading and "busting myths"!
Core to Atlassian’s approach to security in the cloud are four key components. First, Atlassian has established a firm commitment to be the leader in cloud and product security. Second, they strive to meet all requirements defined by their customers regarding cloud security. While doing so, Atlassian is also driven to exceed industry security standards and certifications. Third, Atlassian has worked to establish and maintain transparency regarding its processes and all related metrics. Paired with this self-implemented transparency, they actively encourage competitors to follow suit, all with the goal of benefitting all customers across all platforms. And finally, Atlassian works diligently to identify and isolate existing security threats to their platform, while anticipating and planning for future threats so as to limit the overall effects.
A large majority of businesses (94%) who’ve already made the transition have indicated the move to the cloud has increased levels of security. Yes, you read that correctly - the move to the cloud made it better, not worse. This is in addition to increases to bottom-line profits, overall productivity, and innovation among other benefits.
Myth #1: On-prem is more secure than cloud
Familiar with the phrase, “if it sounds too good to be true, then it probably is”? It’s quite appropriate in this instance regarding the misconception of the typical, on-prem setup being more secure than a cloud instance.
According to a 2019 Gartner forecast report, “By 2022, up to 60% of organizations will use an external service provider’s cloud-managed service offering, which is double the percentage of organizations from 2018.” Cloud service providers (CSPs) like Atlassian are clearly aware, with this being the foundation of their work, that being able to maintain their customer’s data integrity consistently and reliably is incredibly important.
For some beholden to maintaining their data and infrastructure on-prem, oftentimes this boils down to the simple idea of having their data physically close. If they can walk by the server room and see it all right before their eyes, somehow this mistakenly offers reassurance it must be “safe”. In the end, the actual physical location has little to nothing to do with the actual level of security. What ends up being most important is a combination of access and control.
In a standard on-prem scenario, a user’s primary login credentials give them access to the entire system. This single line of defense, although convenient for the employee, is rife with issues should their credentials become compromised. The attacker now has access to everything beyond that one security defense. In essence, “game over”.
This traditional “castle-and-moat” approach to security essentially protects everything inside the organization from what lay outside the firewall. Once past the firewall, either legitimately or not, all users and their devices were then trusted. Recall from your early school days the story of the Trojan horse. Once they were past the single outer perimeter wall and inside, the intruders could pretty much do whatever they wanted.
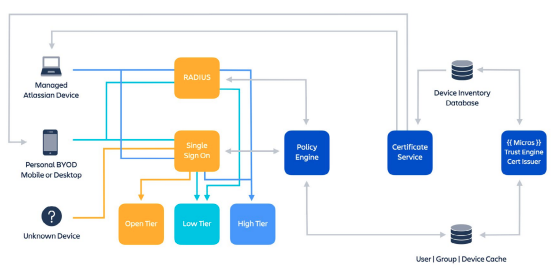
Atlassian’s cloud platform takes a different approach, utilizing a ZeroTrust approach. That is, each tool that every employee touches, verifies login details before moving onto the next layer or tool acting as multi-layered security gates. With this approach, the Trojan horse may have made it past an initial layer of security, but once the plan was discovered, all the additional fortified layers beyond it would’ve protected the city of Troy and all those inside.
The most important rule of ZeroTrust is “never trust, always verify”. Atlassian secures its own corporate network, applications, and cloud environments using this approach. Some organizations mistakenly believe that simply using a Mobile Device Management (MDM) solution, where only trusted devices may access network resources, solves the problem. Here again, this practice lacks specific details.
ZeroTrust is built upon a foundation of dynamic policy decisions that encompasses multiple factors to determine whether a user should be allowed, or denied, access at a per-resource level. Atlassian has created three tiers on their own network upon which ZeroTrust operates. These tiers define what services are available based on their relative level of criticality and sensitivity:
- Open Tier
- Services that can be accessed by any successfully authenticated corporate user.
- Low Tier
- Those services available only when accessed via an authenticated corporate user who is using a trusted, Atlassian-owned device. Additionally, personal devices enrolled into Atlassian’s MDM solution (referred to as Bring Your Own Device or BYOD).
- High Tier
- Services that are made available only when the user has successfully authenticated using an Atlassian-owned, corporate device. Further, production services access via their corporate network requires a High Tier device in addition to Security Assertion Markup Language (SAML). In short, SAML is an XML-based open-standard, where an identity partner (IdP) and a service provider (SP) may transfer identity data between them
Myth #2: My teams prioritize security better than cloud vendors
If you were to ask ten of your developers (should you have that many) where they place the issue of security among the list of “must-haves”, you would get ten different answers. In the instance where your staff size is smaller and there is no dedicated team working specifically on building and testing your on-prem security measures, you have some real challenges ahead of you.
Before an organization can expect its developers to make security a priority, the management and administrators of the organization must do so. Once management gives security a higher priority, all teams, including developers will follow suit. In an often referenced survey conducted by the Ponemon Institute, 71% of developers indicated they felt issues of security had not been properly addressed during the software development cycle. In that same survey, 61% of the security respondents and 65% of developers indicated they do not test mobile applications at any point in production, development, or quality assurance (QA) processes.
When your entire foundation is built upon ensuring the highest level of security for it to survive - as is the case for a cloud infrastructure provider - you can guess security is job one. Atlassian ensures security is always the priority through the implementation of rigorous testing, end-to-end data encryption, and extensive disaster recovery planning.
Atlassian is continually improving its security program, not simply relying on the status quo. This involves a great deal of internal self-assessment as well as third-party independent evaluations of their processes. For example in 2020, in addition to their own appraisal of their security protocols, a peer assessment of their overarching Trust and Security Program took place. Recommendations were then used to remove any gaps that were identified and implement opportunities for improvement.
Regardless of the size of the user, each is guaranteed the same level of exceptional, enterprise-grade security. Your developers can worry about developing, designers can design and your support staff can go back to supporting your entire staff. Atlassian has them covered.
Myth #3: My teams are not on the cloud yet
Really? You might want to rethink that belief.
Let us introduce you to the term “Shadow IT”. Shadow IT is the use of any system, device, software, application, or service without explicit knowledge or permission from your IT team. Often employees will find workarounds to official systems or policies for the sake of, at least in their minds, being more efficient.
Maybe they want to use their own laptop to access the corporate network from home versus taking their company-issued one. Or possibly they believe they’ve found a more user-friendly file sharing service or messenger platform than the one that the company has implemented. In essence, any application a user makes use of for business purposes without involving their organization’s IT group is considered a Shadow IT application.
However, in addition to the physical hardware that hasn’t been approved for use, Shadow IT includes the use of authorized cloud-based services. This includes software as a service (SaaS), infrastructure as a service (IaaS), and platform as a service (PaaS). The lack of visibility as to what these devices and application services are accessing through the use of functionality such as file sharing, storage, or collaboration presents enormous risks to an organization.
Consider an example of an employee making use of cloud-based applications accessed via OAuth token. Many major SaaS applications like Office 365 make use of OAuth tokens. These can be convenient as they make use of a user’s existing credentials. The issue is they also include permissions tied to the core application itself, such as Office 365. Sensitive corporate data can then be accessed using the built-in file sharing and communication tools.
As Jay Heiser, Vice President Analyst at Gartner said in 2019, the question should not be “Is the cloud secure?” but rather “am I using the cloud securely?” It’s not whether or not you should use the cloud - you should. However, you must determine if your team has the proper tools needed to make full use of cloud infrastructure safely.
As always, if you would like to try Atlassian Cloud or have any questions, please feel free to reach out to us at Seibert Media.